Introduction
On 9th August 2022, I and my colleague Ashutosh Mahajan were testing a production-based android application as a part of our practice. The application on which we were testing was related to an EV company.
Brief about the app
The app is used by EV users use to locate charging stations and pay for the facility.
Findings
Broken Access Control
As we started our testing, we instantly found a broken authentication. The OTP which was sent at the time of registration and password reset were given beforehand in the response (this plays a very crucial role later on).
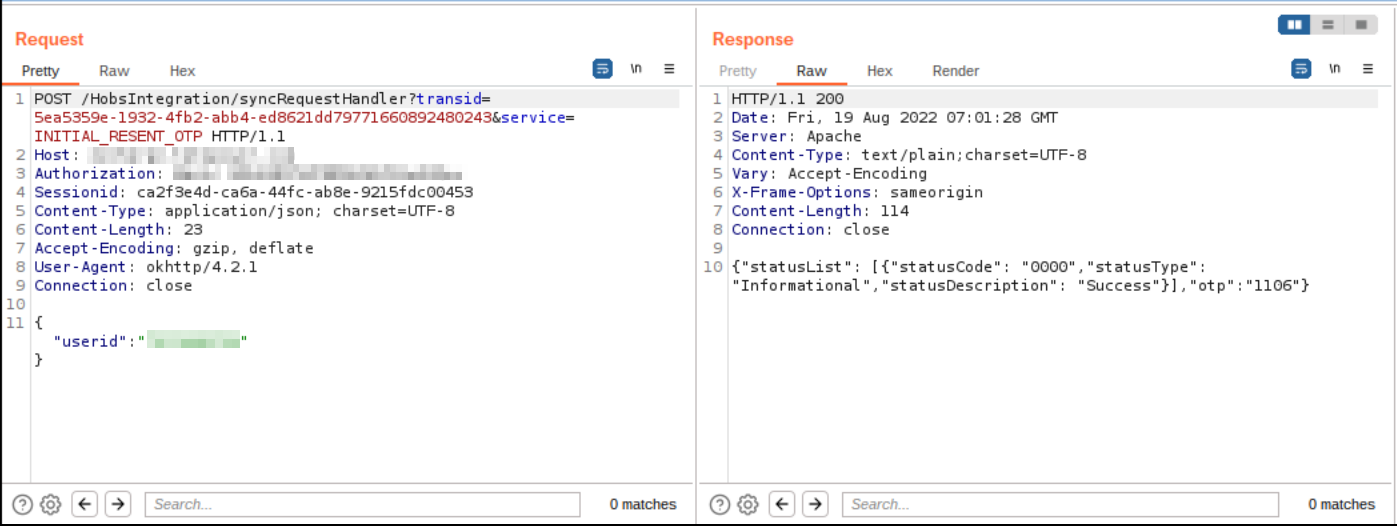
Indirect Object Reference
As the app was specifically developed to pay at charging station via the application. So, they integrated two wallets for the payments at the EV charging stations. One being PayTm wallet and the other was the application’s built-in wallet. So whenever, any user topped-up their wallet, an invoice was created for that transaction. The request which was responsible for downloading the invoice had a invoiceNo parameter that was vulnerable to IDOR.
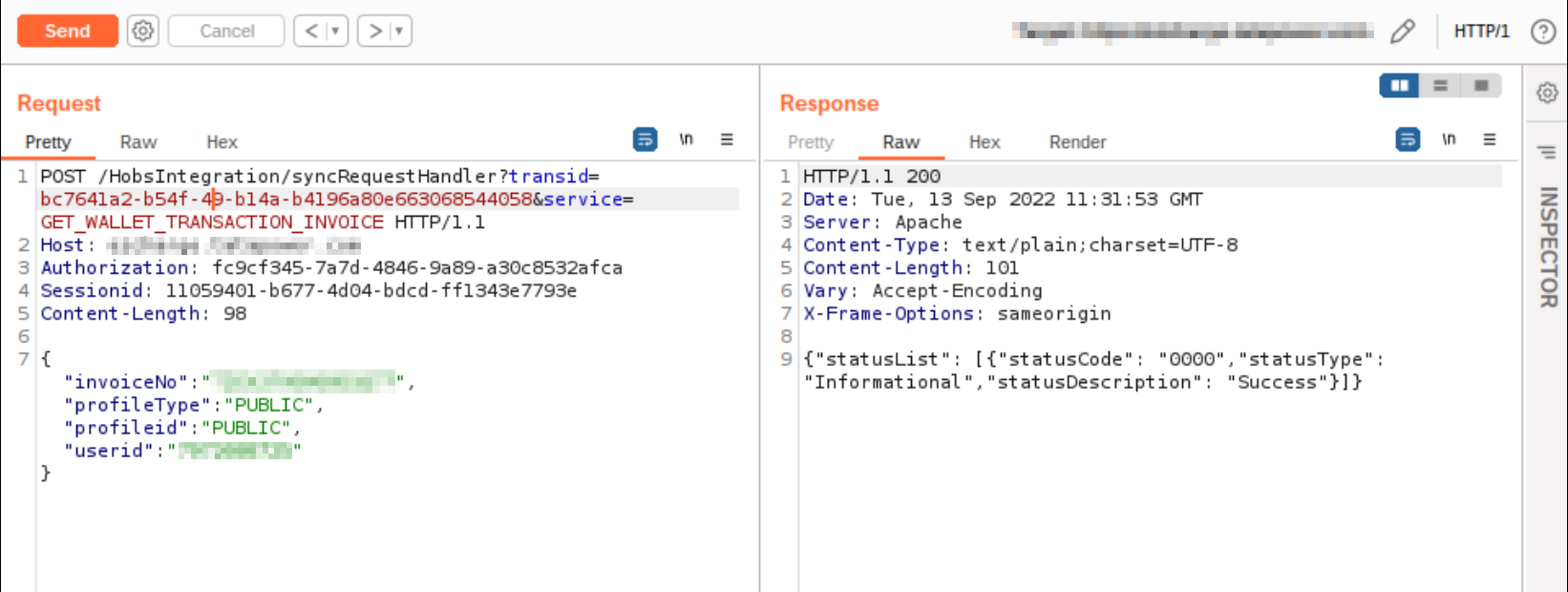
When examining the above request, if we change the invoiceNo to another invoiceNo of our other testing account, we got a valid response and we were able to download their invoice.
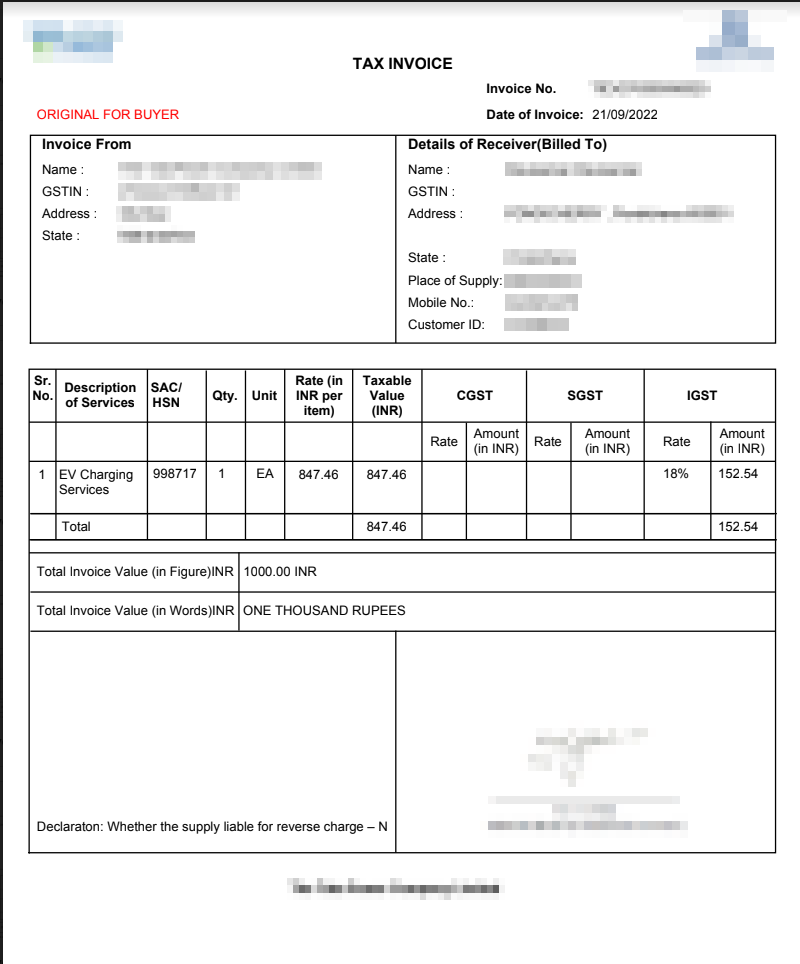
The invoice had details like Name, GST No., Address, Mobile No., Customer ID., and transaction details.
Chaining the above mentioned findings
For demonstration purposes, we created two users Test1 and Test2 . Test1 being the attacker and Test2 being a normal customer.
- We login using Test1 and we then enumerate for invoiceNo of Test2.
- After, enumerating the invoice which belonged to Test2, we found its mobileNo from it.
- Now heading back to the login page, to login as Test2 we entered their mobileNo and clicked on the forgot password option to reset their password.
- As we were getting the OTP in the response, and also the application was vulnerable to response manipulation we were able to change the password of Test2 without their consent and without them knowing.
- And on the side of Test2, they were completely unaware of the fact that their password is changed and their account has been compromised.
More Findings
This app not only has the above mentioned two major vulnerabilities but also there are other severe vulnerabilities such as response manipulation, no proper validation of phone number which could be exploited to create multiple bot accounts, clear text transmission of credentials, no rate limit, and many more such vulnerabilities.
Note
On 24/10/2022, we were able to get invoices of more than 25,000+ customers.

Conclusion
After linking all of these vulnerabilities, its impact is high. It affects the company and the customer both. This could be further escalated to monetary loss of customers and harming the nature of the app, as there are no strict security policies implemented in order to make the app safe.
Update as of March 2023
As of 01/03/2023 all the reported issues have been fixed.
